Twitter is more than just a social media platform; it's a digital battleground where information wars are fought daily. But what happens when the platform itself becomes the target? Distributed Denial of Service (DDoS) attacks on Twitter are becoming increasingly common, leaving users frustrated and businesses at risk. In this article, we'll dive deep into the world of DDoS Twitter attacks—what they are, how they work, and most importantly, how to protect yourself.
Picture this: you're scrolling through your Twitter feed, catching up on the latest news or engaging with your favorite influencers. Suddenly, the platform slows down to a crawl, or worse, becomes completely inaccessible. Sound familiar? It's not just a random glitch—it could very well be a DDoS attack in action.
Now, before we get into the nitty-gritty, let's make one thing clear: DDoS attacks aren't just a Twitter problem. They affect websites, services, and networks across the globe. But when it comes to a platform as influential as Twitter, the stakes are higher. So buckle up, because we're about to break it all down for you in a way that's easy to understand yet packed with actionable insights.
- Marie Temara Onlyfans A Comprehensive Guide To Her Career Content And Achievements
- Remote Iot Vpc Review Unlocking The Future Of Connected Systems
What Exactly is a DDoS Attack?
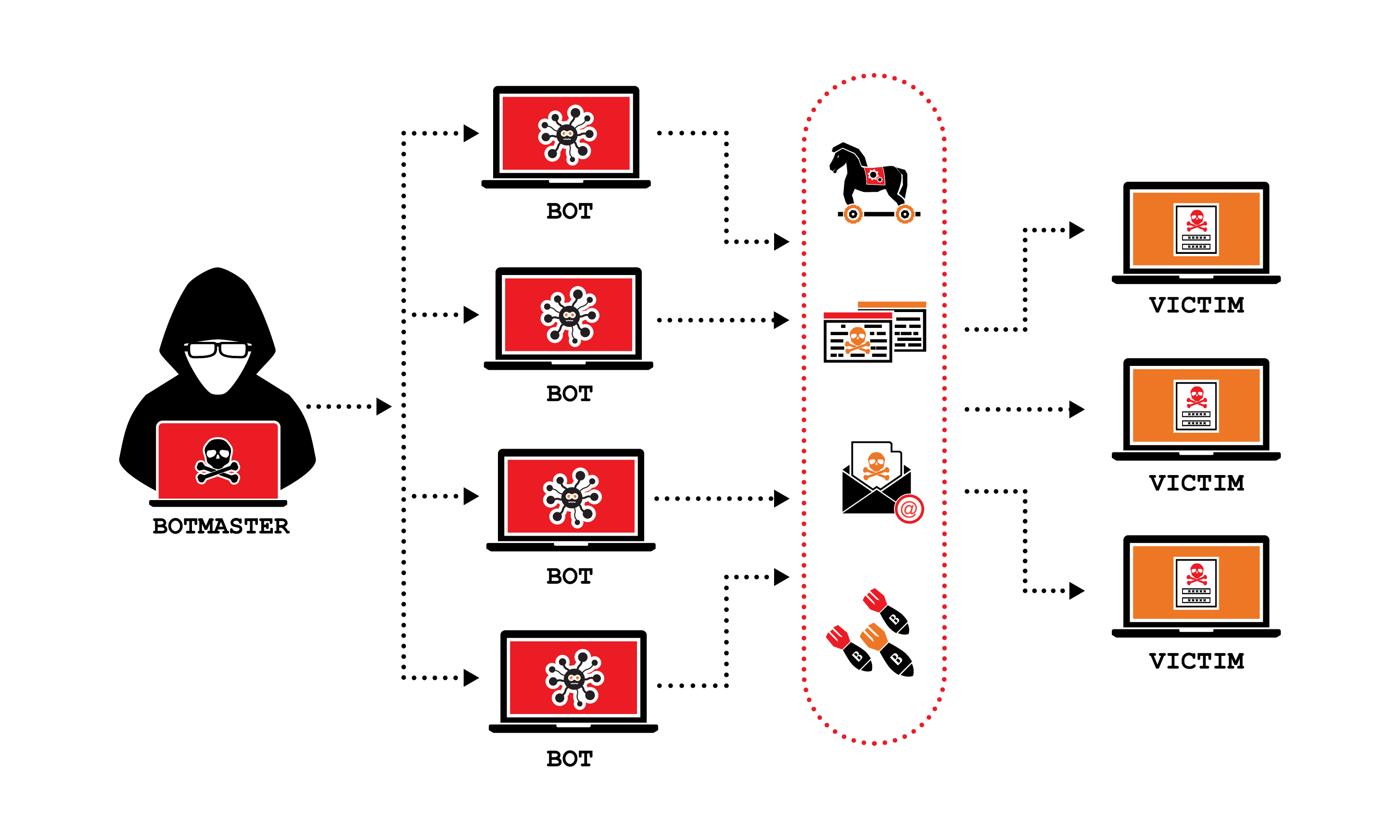
Let's start with the basics. A Distributed Denial of Service (DDoS) attack is essentially a cyber assault designed to overwhelm a network or service, making it unavailable to its intended users. Think of it like a traffic jam on the internet. Instead of cars, you've got a massive influx of requests flooding the system until it collapses under the pressure.
DDoS attacks are often carried out using botnets—armies of compromised devices that are remotely controlled by attackers. These devices can range from personal computers to IoT gadgets like smart refrigerators and security cameras. Once under the attacker's control, these devices are used to bombard the target with traffic until it can no longer handle the load.
Now, here's the kicker: DDoS attacks aren't just about taking down websites. They can also be used as a smokescreen for more sinister activities, like data breaches or financial fraud. Scary stuff, right?
Why Do Hackers Target Twitter?
Twitter is a goldmine for hackers. With millions of active users and real-time updates, it's the perfect platform for spreading misinformation, influencing public opinion, or even launching coordinated attacks. But why would someone want to take down Twitter in the first place?
- Political motives: In some cases, DDoS attacks are politically motivated. Activist groups or nation-states might target Twitter to silence dissenting voices or disrupt communication during critical events.
- Financial gain: Ransom DDoS attacks are on the rise. Attackers might threaten to take down Twitter unless the company pays up. It's a high-stakes game of chicken that no one wants to play.
- Reputation damage: Let's face it—no one likes being the victim of a cyberattack. A successful DDoS attack on Twitter can tarnish the platform's reputation, leading to a loss of users and advertisers.
And let's not forget the thrill factor. For some hackers, launching a DDoS attack is less about the money and more about proving they can do it. It's like digital graffiti on a massive scale.
How DDoS Attacks Impact Twitter Users
When a DDoS attack hits Twitter, the effects are felt by everyone. From casual users to businesses, no one is immune. Here's how it impacts different groups:
For Individual Users
Imagine trying to tweet about the latest celebrity drama or a breaking news story, only to find that Twitter is down. Frustrating, right? For individual users, DDoS attacks mean lost opportunities to engage with their audience, share information, or simply stay connected. It's like being stuck in a digital blackout.
For Businesses
Twitter is a powerful marketing tool for businesses. It's where brands build relationships, promote products, and stay relevant in a fast-paced digital world. But when Twitter goes down due to a DDoS attack, businesses lose valuable visibility and engagement opportunities. It's not just about missed tweets—it's about missed revenue.
And let's not forget the trust factor. If customers can't rely on a brand's Twitter presence, they might start questioning the brand's overall reliability. Not good.
The Anatomy of a DDoS Attack on Twitter
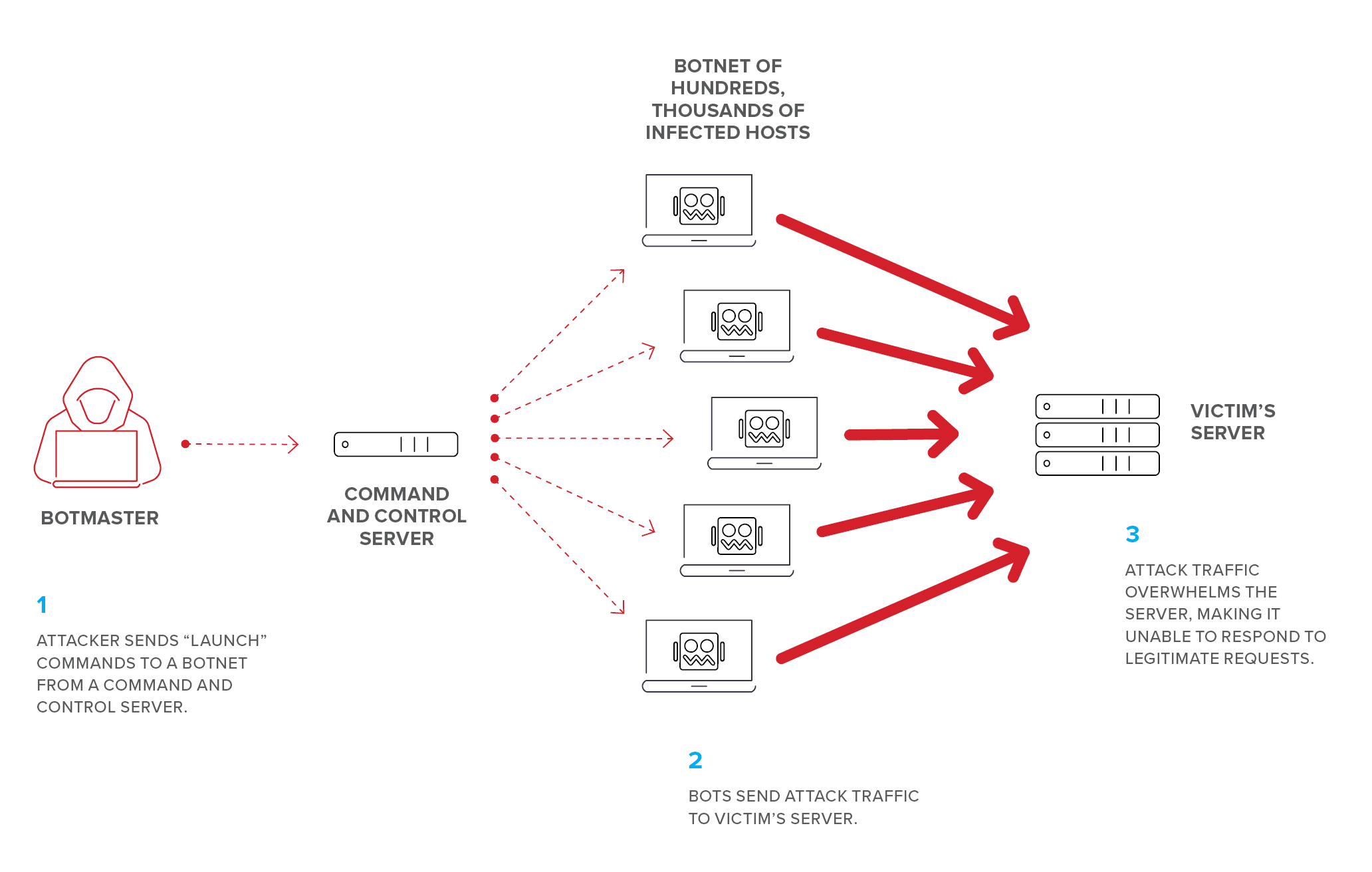
So, how exactly does a DDoS attack work? Let's break it down step by step:
- Reconnaissance: Attackers scout for vulnerabilities in Twitter's infrastructure. This could involve identifying weak points in the platform's defenses or exploiting known security flaws.
- Botnet creation: Once the target is identified, attackers begin assembling their botnet army. This involves infecting as many devices as possible with malware, turning them into unwitting participants in the attack.
- Attack launch: With the botnet in place, the attackers unleash a flood of traffic on Twitter's servers. This traffic can take many forms, including HTTP requests, ICMP packets, or UDP floods, depending on the attack's objectives.
- Impact: As the traffic overwhelms Twitter's servers, the platform begins to slow down or become completely inaccessible. Users experience timeouts, error messages, or an inability to load pages.
It's a well-coordinated operation that can bring even the most robust platforms to their knees. And the worst part? It can happen in a matter of minutes.
Types of DDoS Attacks on Twitter
Not all DDoS attacks are created equal. Here are some of the most common types that could target Twitter:
Volume-Based Attacks
These attacks focus on overwhelming Twitter's bandwidth with sheer volume. Think of it like trying to pour a fire hose through a garden hose—it just doesn't work. Common examples include ICMP floods and UDP floods.
Protocol Attacks
Protocol attacks exploit weaknesses in the networking protocols that Twitter uses to communicate. By overwhelming intermediate resources like firewalls or load balancers, attackers can cripple the platform without directly targeting its servers.
Application Layer Attacks
These attacks target specific applications or services within Twitter's infrastructure. For example, an attacker might flood the platform's login system with fake authentication requests, making it impossible for legitimate users to log in.
Each type of attack requires a different defense strategy, which is why understanding the threat landscape is crucial for protecting against DDoS attacks.
How Twitter Fights Back Against DDoS Attacks
Twitter isn't sitting idly by while hackers wreak havoc on its platform. The company has invested heavily in cybersecurity measures to detect and mitigate DDoS attacks. Here's a glimpse into their arsenal:
- Advanced firewalls: These act as a first line of defense, filtering out malicious traffic before it reaches Twitter's servers.
- DDoS mitigation services: Twitter partners with third-party providers to absorb and neutralize large-scale attacks. Think of it like outsourcing your security to a team of experts.
- Real-time monitoring: By keeping a close eye on network activity, Twitter can quickly identify and respond to suspicious behavior before it escalates into a full-blown attack.
But even with all these measures in place, DDoS attacks remain a persistent threat. That's why it's important for users and businesses to take their own precautions.
Protecting Yourself from DDoS Twitter Attacks
You might be wondering, "What can I do to protect myself from DDoS attacks on Twitter?" The truth is, there's no foolproof way to completely eliminate the risk. But there are steps you can take to minimize the impact:
For Individual Users
- Stay informed: Keep an eye on Twitter's official announcements and news outlets for updates on DDoS attacks.
- Use alternative platforms: If Twitter goes down, consider using other social media platforms or messaging apps to stay connected.
- Report suspicious activity: If you notice any unusual behavior on Twitter, report it to the platform immediately. Every bit of information helps.
For Businesses
- Invest in cybersecurity: Protect your own infrastructure from DDoS attacks by implementing robust security measures.
- Have a backup plan: Develop a communication strategy that doesn't rely solely on Twitter. This could include email newsletters, blogs, or other social media channels.
- Engage with your audience: Build strong relationships with your followers so they're more likely to stick around during a crisis.
By taking these proactive steps, you can ensure that you're prepared for whatever the digital world throws your way.
Real-World Examples of DDoS Attacks on Twitter
Let's take a look at some notable DDoS attacks that have targeted Twitter in the past:
The 2010 Attack
One of the earliest recorded DDoS attacks on Twitter occurred in 2010. The attack was reportedly carried out by a group of hackers who were unhappy with a particular user's content. While the attack was relatively short-lived, it highlighted the platform's vulnerability to cyber threats.
The 2016 Dyn Attack
Although not directly targeting Twitter, the 2016 Dyn attack had a ripple effect that impacted the platform. The attack targeted Dyn, a major DNS provider, causing widespread outages across the internet, including Twitter. It served as a wake-up call for companies to strengthen their cybersecurity defenses.
These real-world examples underscore the importance of staying vigilant in the face of evolving cyber threats.
The Future of DDoS Attacks on Twitter
As technology continues to evolve, so too do the methods used by attackers. Here are some trends to watch out for in the world of DDoS attacks:
- AI-powered attacks: Attackers are beginning to use artificial intelligence to automate and enhance their DDoS campaigns, making them harder to detect and mitigate.
- IoT botnets: With the proliferation of connected devices, attackers have more potential recruits for their botnets than ever before.
- Multi-vector attacks: Attackers are combining different types of DDoS attacks to create more complex and resilient threats.
While these trends may seem daunting, they also present opportunities for innovation in cybersecurity. By staying ahead of the curve, Twitter and its users can better protect themselves from future attacks.
Conclusion: Stay Safe and Stay Connected
In conclusion, DDoS attacks on Twitter are a serious threat that can disrupt communication, damage reputations, and cause financial losses. But with the right knowledge and tools, you can minimize their impact and continue to enjoy the platform safely.
So, what can you do next? Start by educating yourself and your team about DDoS attacks and their potential consequences. Implement cybersecurity best practices, and don't be afraid to speak up if you notice anything suspicious. Together, we can make the digital world a safer place for everyone.
And remember, if you found this article helpful, don't forget to share it with your friends and followers. Knowledge is power, and staying informed is the first step toward protecting yourself from cyber threats.
Table of Contents:
- What Exactly is a DDoS Attack?
- Why Do Hackers Target Twitter?
- How DDoS Attacks Impact Twitter Users
- The Anatomy of a DDoS Attack on Twitter
- Types of DDoS Attacks on Twitter
- How Twitter Fights Back Against DDoS Attacks
- Protecting Yourself from DDoS Twitter Attacks
- Real-World Examples of DDoS Attacks on Twitter
- The Future of DDoS Attacks on Twitter
- Conclusion: Stay Safe and Stay Connected
- Daniel Sunjata A Journey Through Acting And Activism
- Ari Kytsya Onlyfans A Comprehensive Look Into Her Career And Success